Cisco Ise 2.4 Ad Integration
The purpose of this blog post is to document the configuration steps required to configure Wireless 802.1x authentication on a Cisco vWLC v8.3 using Cisco ISE 2.4 as the RADIUS server.
- Cisco Ise 2.4 Ad Integration Module
- Cisco Ise 2.4 Ad Integration Tutorial
- Cisco Ise 2.4 Ad Integration Tool
- Cisco Ise 2.4 Ad Integration System
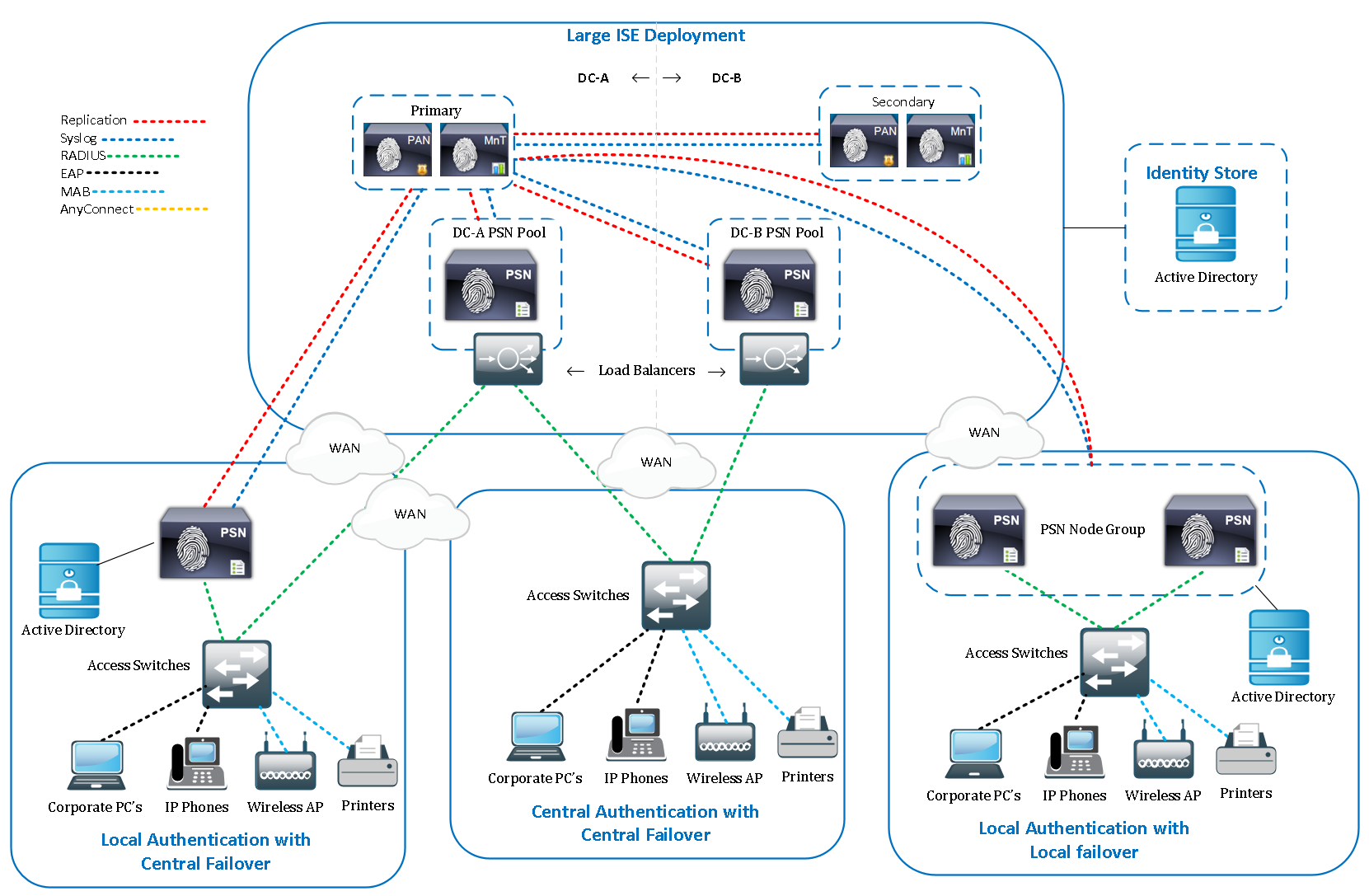
WLC Configuration
Define AAA Servers
- Login to the WLC WebGUI
- Click Advanced
- Navigate to Security > AAA > RADIUS > Authentication
- Click New
- Define the IP address of the RADIUS Server (ISE)
- Define the Shared Secret
- Ensure Support for CoA is Enabled
- Click Apply
- Navigate to Security > AAA > RADIUS > Accounting
- Click New
- Define the IP address of the RADIUS Server (ISE)
- Define the Shared Secret
- Click Apply
Create WLAN
Cisco Ise 2.4 Ad Integration Module
- Navigate to WLANs > WLANSs > WLANs
- Select Create New and click Go
- Define a Profile Name e.g. LAB_WLAN
- Define a SSID e.g. LAB_SSID
- Define an ID e.g. 1
- Click Apply
In this short video, I show you how to integrate Microsoft Active Directory with Cisco ISE. Oct 15, 2015 Active Directory Integration with Cisco ISE 2.x. Identity Rewrite. This feature allows Cisco ISE to modify the username that is received from the client or a certificate, before sending it toward Active Directory for authentication.
- Under the General tab, ensure the Status is Enabled and Security Policies is [WPA2][Auth (802.1x)]
- Under the Security tab, select AAA Servers
- Ensure the Auth Called Station ID Type is AP MAC Address:SSID
- From the drop down list select the previously defined Authentication and Accounting Servers
- Ensure Interim Update is selected
- Scroll down and remove LOCAL and LDAP, ensure only RADIUS is used for authentication
- Under the Advanced tab, tick the box for DHCP Addr. Assignment
- Under the Radius Client Profiling section, tick the box for DHCP Profiling and HTTP Profiling
- Click Apply
AP Groups
- Navigate to WLANs > Advanced > AP Groups
- Click Add Group
- Define a name for the group, e.g. LAB_GROUP
- Click Add
- Click the newly created AP Group
- Define a NAS-ID e.g vWLC
- Click Apply
- Click WLANs tab
- Click Add New
- Select the WLAN SSID from the drop down list, click Add
- Click the APs tab
- Select the AP(s) to add to the Group, click Add APs
NOTE – the AP(s) will now be reconfigured and rebooted
- Click <Back when complete
ISE Configuration
Authentication Policy
- Create or modify the Authentication Policy
- Create a rule to authenticate using PEAP/MSCHAPv2, named appropriately
Rule Name:-
MSCHAPv2
Conditions:-
Network Access-EapAuthentication EQUALS EAP-MSCHAPv2
Wired_802.1x
Use:-
Authorization Policy
- Create new Authorization Rules as per the table below
| Rule Name | Conditions | Profiles |
| Domain Admins | Radius Called-Station-ID MATCHES .*(:)$ LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Admins Wireless_802.1X | PermitAccess |
| Domain Users | Airespace Airespace-Wlan-Id EQUALS 1 LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Users Wireless_802.1X | PermitAccess |
| Domain Computers | LAB_AD-ExternalGroups EQUALS lab.local/Users/Domain Computers Wireless_802.1X | PermitAccess |
| Default | PermitAccess |

When the user connects the AP MAC Address + SSID is sent in the radius packet, this can be used in the Authorization rule to distinguish users from the SSID they are connecting from. The first rule for Domain Admins uses the Called-Station-ID radius attribute with a regex to match the SSID the user is connected to.
In addition to using the Called-Station-ID radius attribute to determine the SSID the user is connected to, if the WLC/AP is Cisco we can use the attribute Airespace-Wlan-Id. For members of the Domain Users group we will use this value. It is important to note the value specified must equal the number of the SSID defined in the WLC SSID configuration.
Cisco Ise 2.4 Ad Integration Tutorial
For Domain Computers we will not require the computer can authenticate from a specific WLAN SSID, just that it is a member of the Domain Computers AD group.
Verification and Testing
With a wireless enabled device login as a user that is a member of the AD group Domain Users. From the ISE logs we can determine the user was matched against the correct Authorization rule and the conditions worked.
Cisco Ise 2.4 Ad Integration Tool
Logoff and login as a user that is a member of the AD group Domain Admins. From the ISE logs we can determine the user was matched against the correct Authorization rule and these conditions also worked.
Cisco Ise 2.4 Ad Integration System
From the detailed output we can determine the AD Group, the NAS-Identifier defined in the AP Group configuration and the Called-Station-ID.
From the WLC we can navigate to Monitor > Clients and determine the client properties. We can determine user2 associated to the correct SSID and used 802.1x authentication, with PEAP as the protocol.
